Edge Computing and IoT: Systems, Management and Security (kartoniertes Buch) | Buchhandlung Schöningh

Techment Technology on Twitter: "Advantages of Edge Computing https://t.co/czzqsGALRn #Data #Cloud #Edge #Computing #Security #technology #AI #IoT Source:https://t.co/f4ZEmk7YBk https://t.co/tZ6kR9k2UU" / Twitter



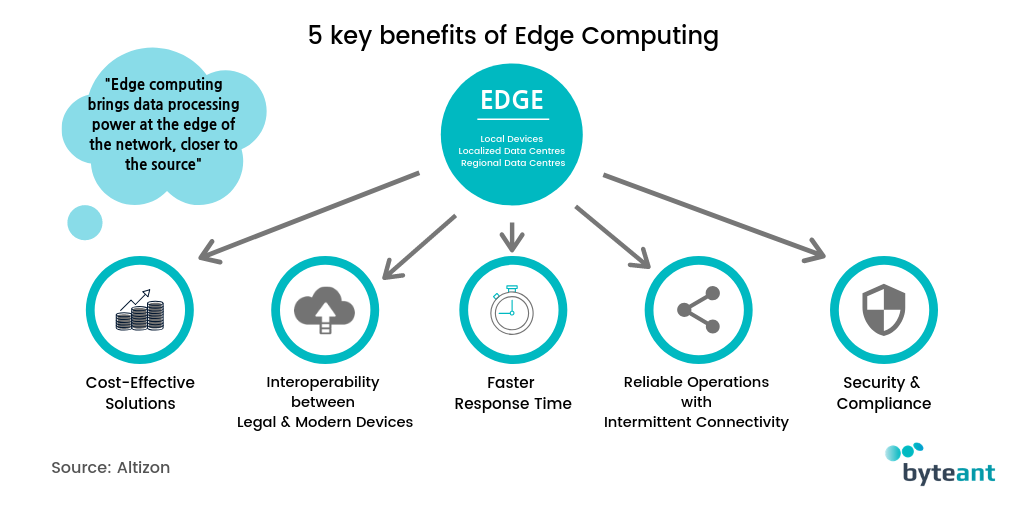
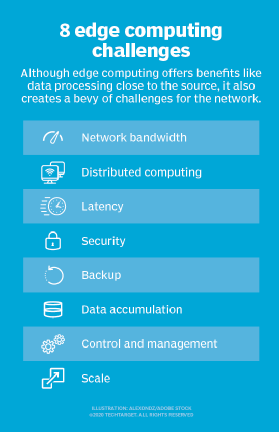



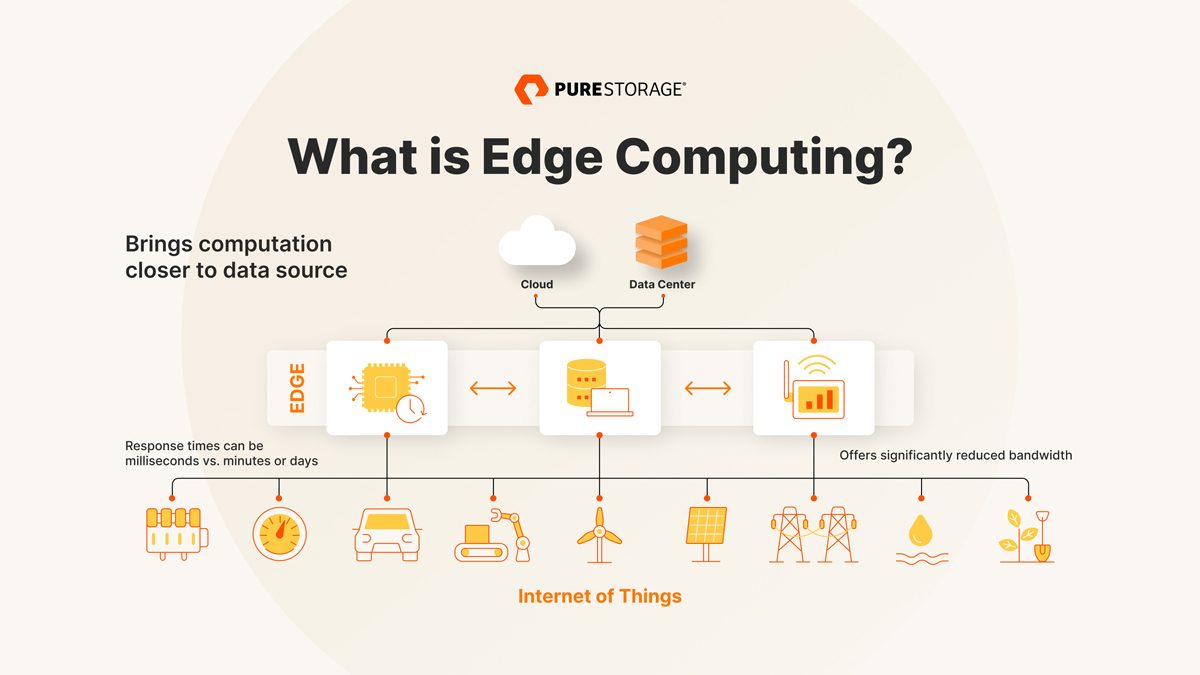
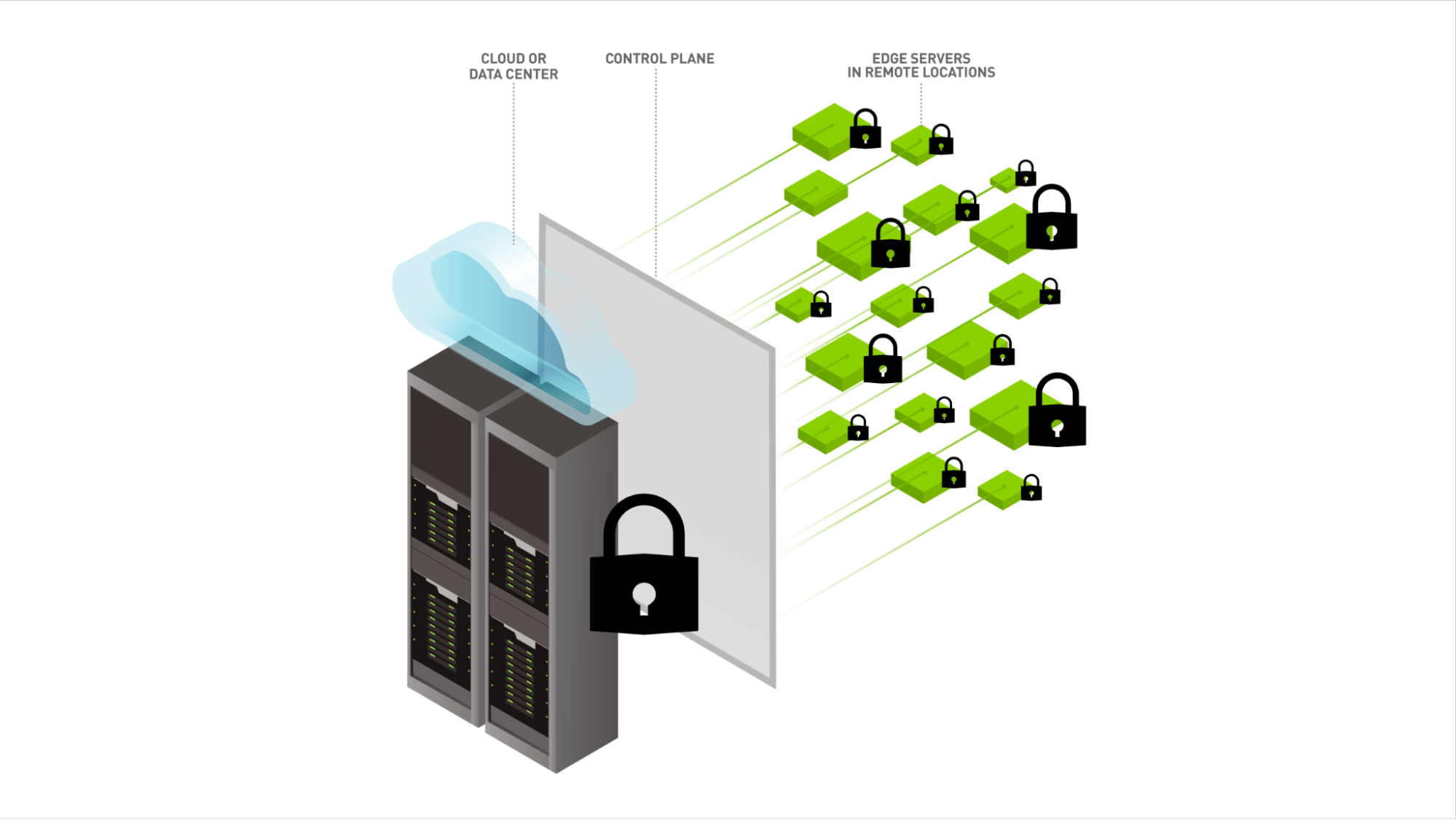


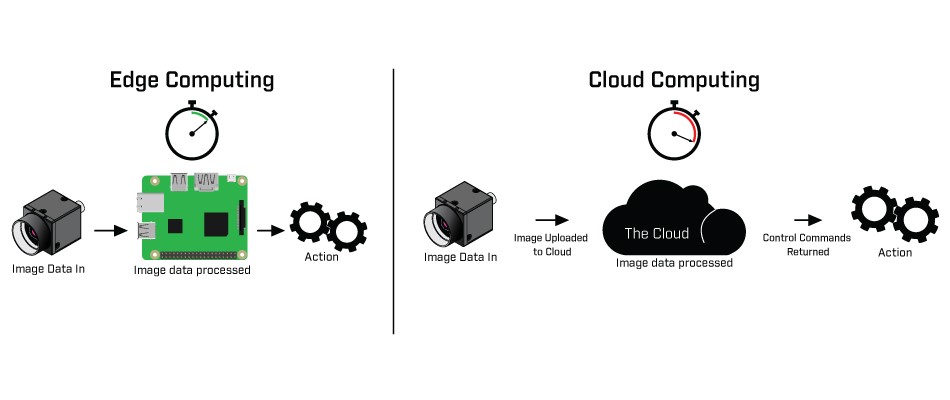
![PDF] Secure Edge Computing in IoT Systems: Review and Case Studies | Semantic Scholar PDF] Secure Edge Computing in IoT Systems: Review and Case Studies | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/6e8133cdf466ac14f1a38f25b21ea74612d7cb97/4-Figure1-1.png)
