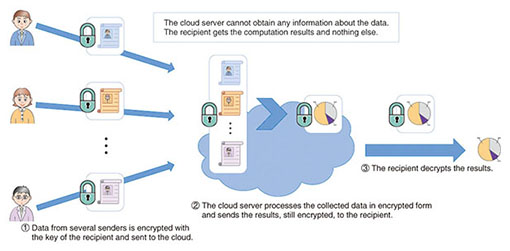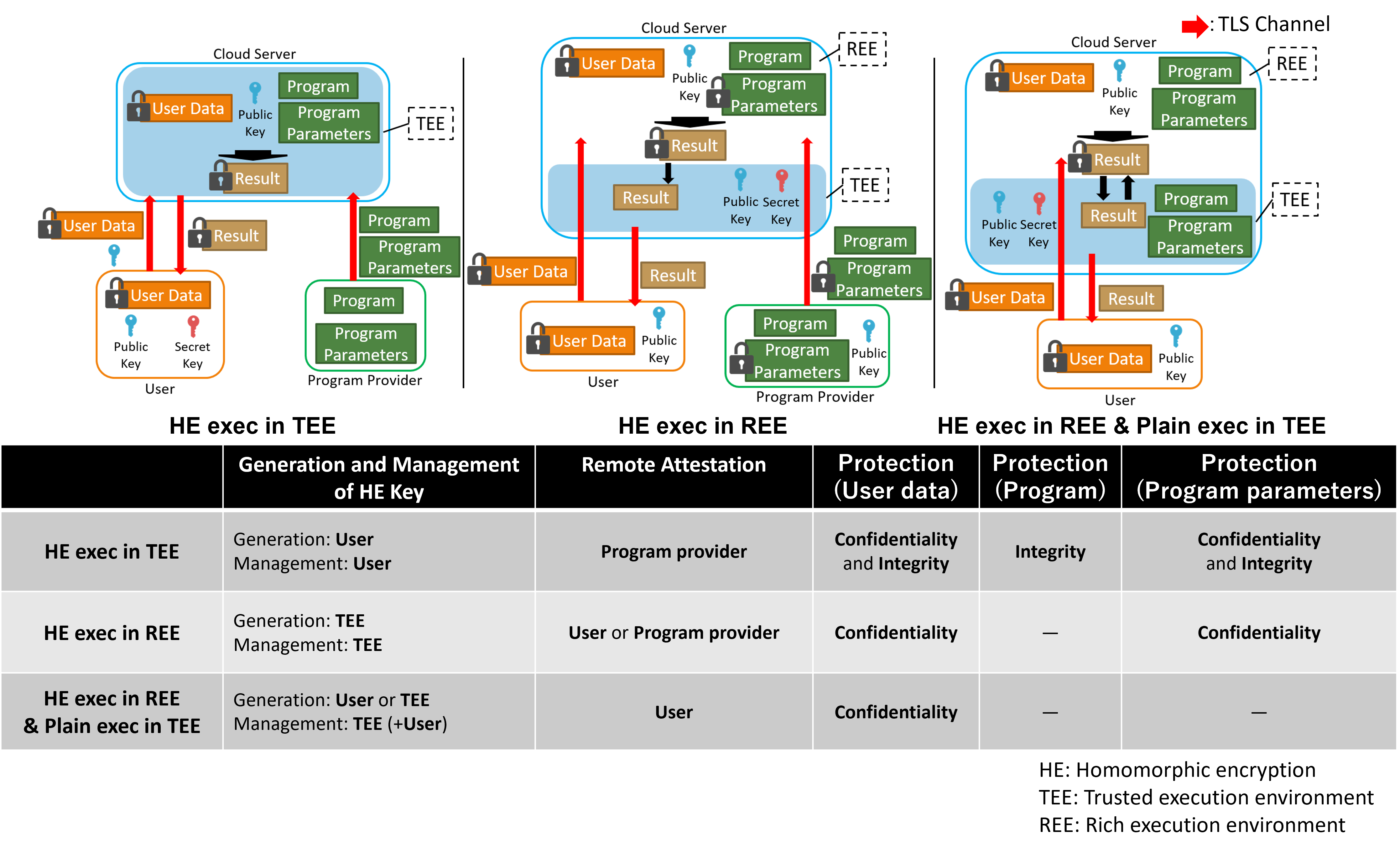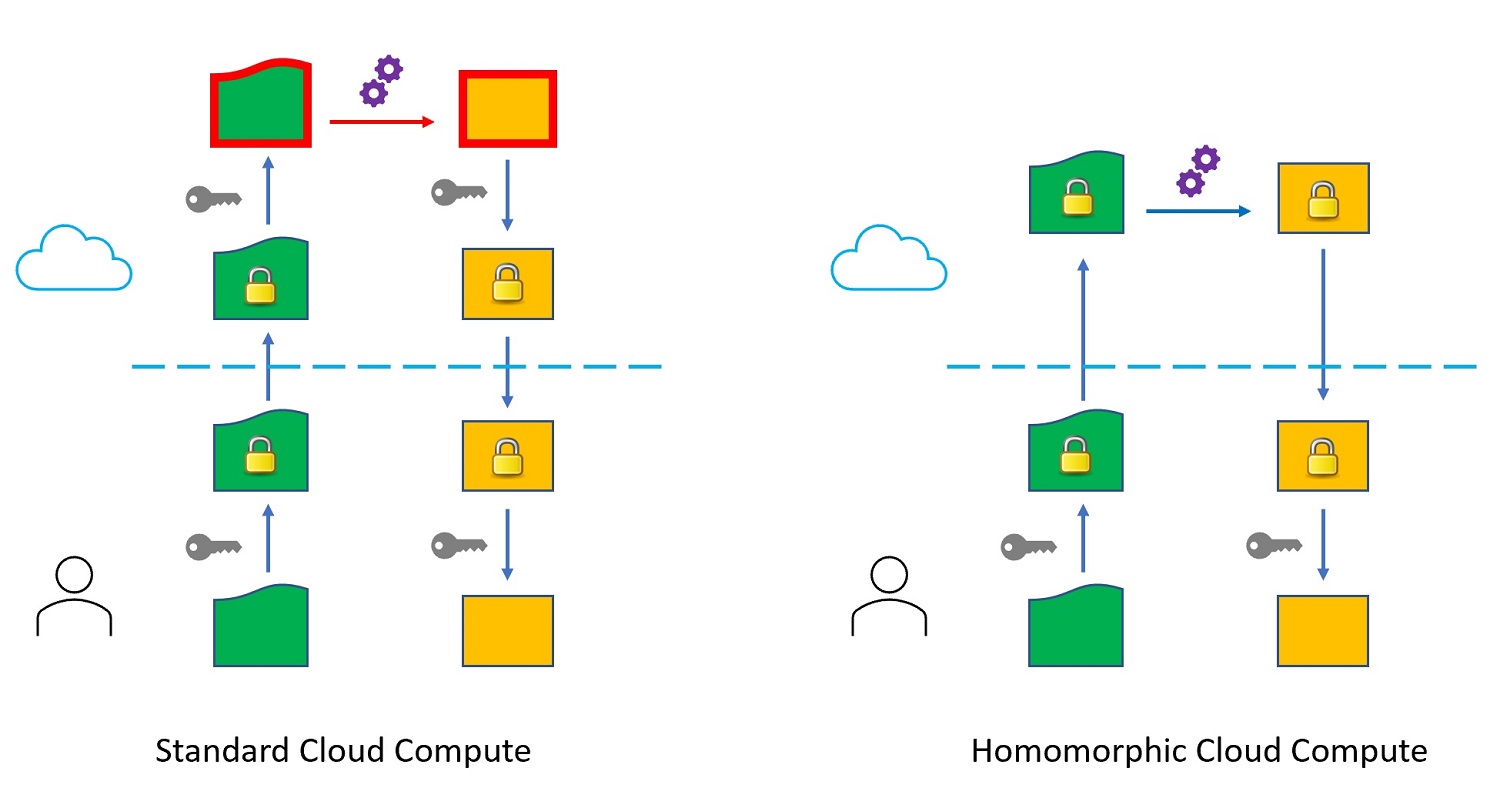
Technologies | Free Full-Text | A Verifiable Fully Homomorphic Encryption Scheme for Cloud Computing Security
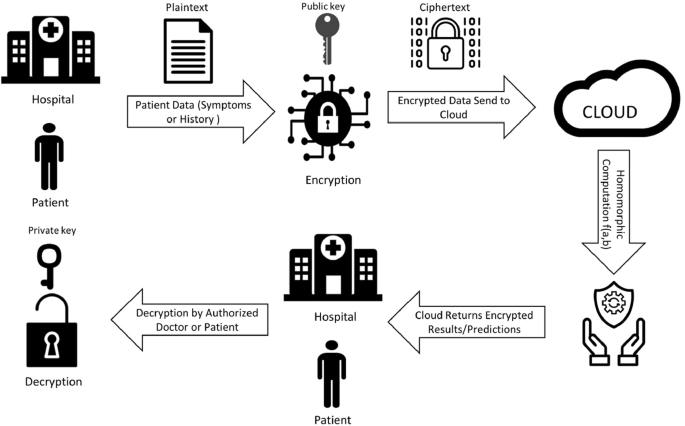
A systematic review of homomorphic encryption and its contributions in healthcare industry | SpringerLink
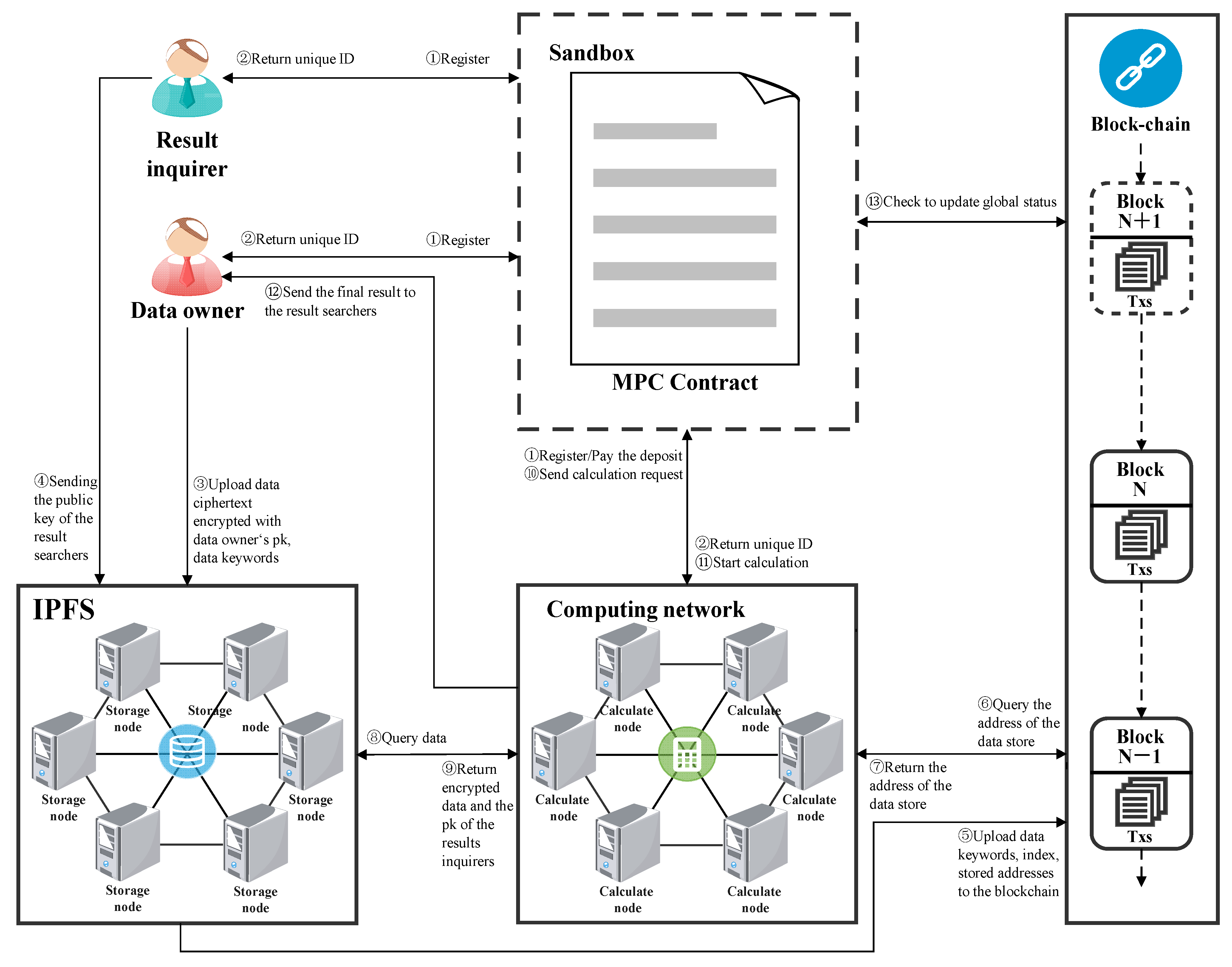
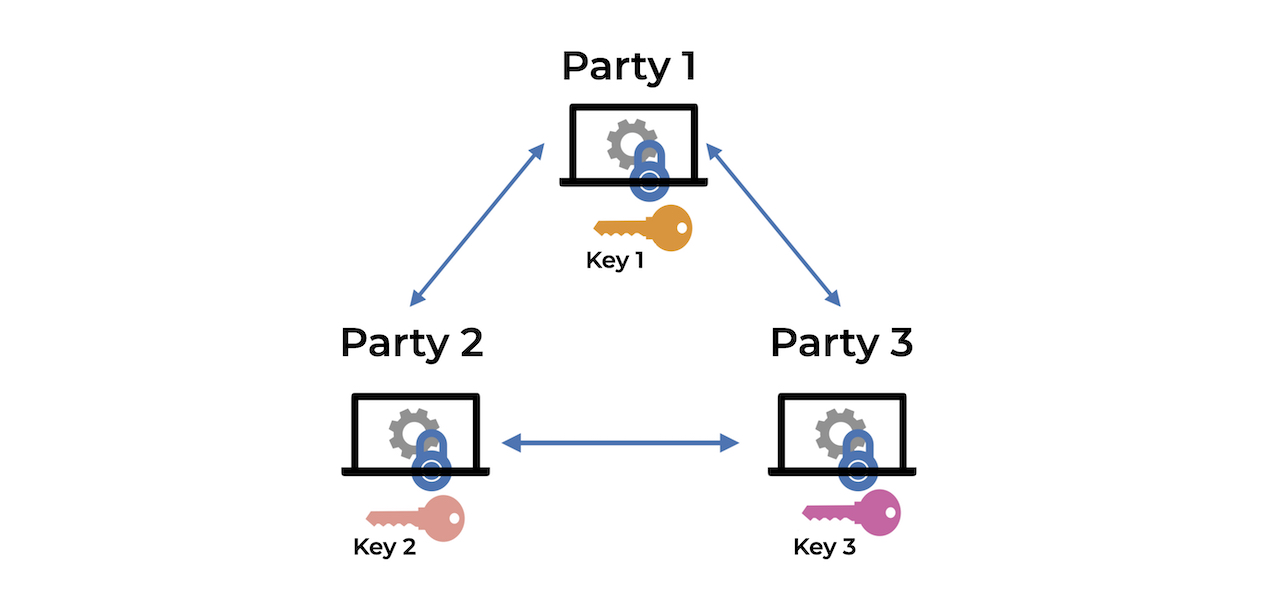
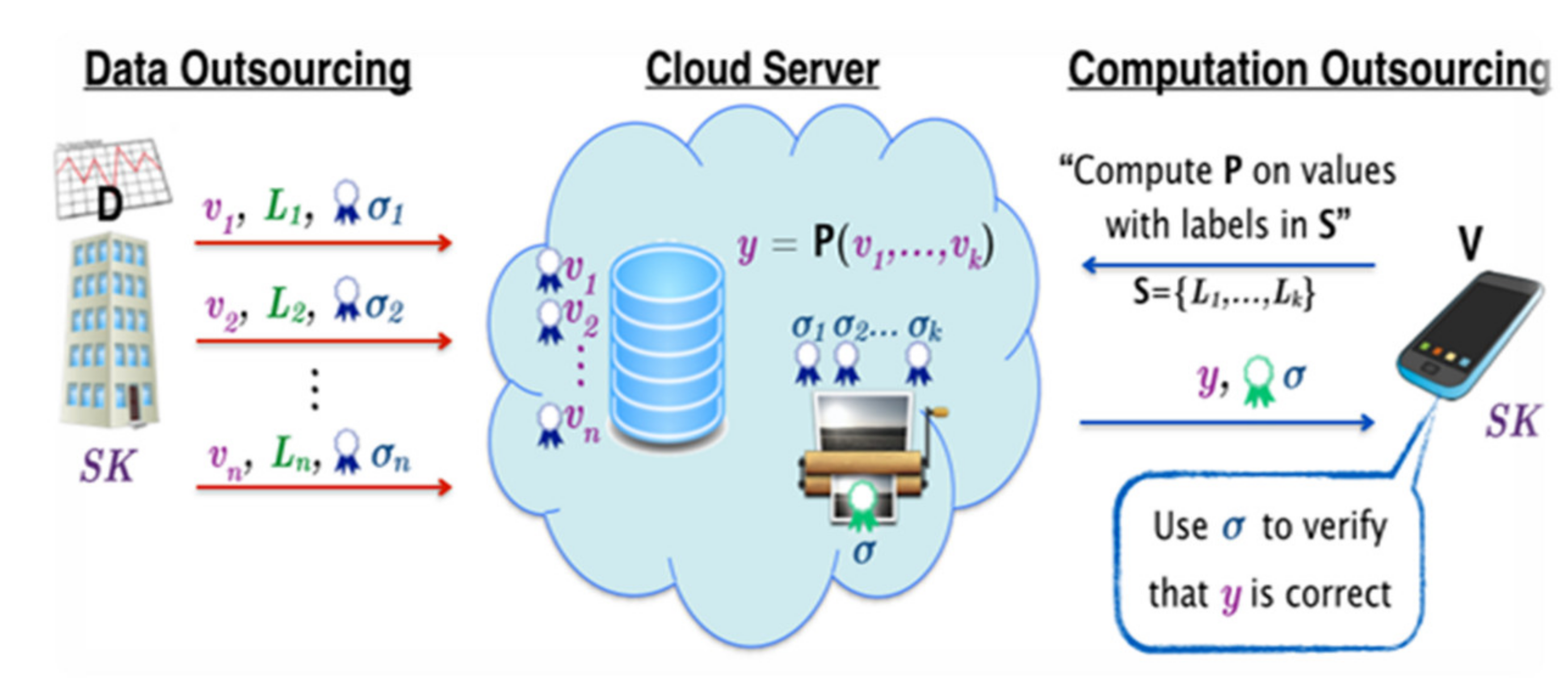
Information | Free Full-Text | A Blockchain-Based Secure Multi-Party Computation Scheme with Multi-Key Fully Homomorphic Proxy Re-Encryption
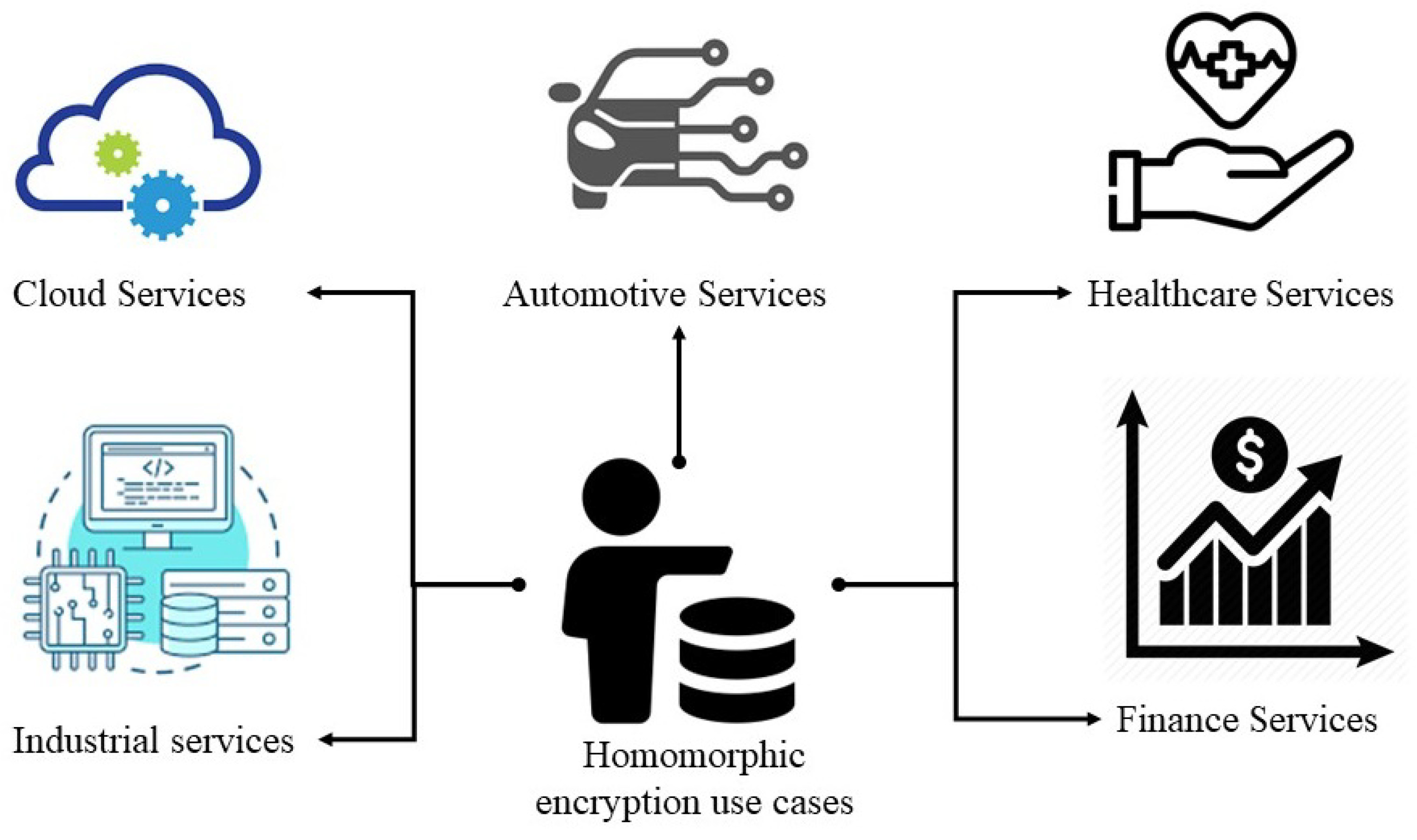
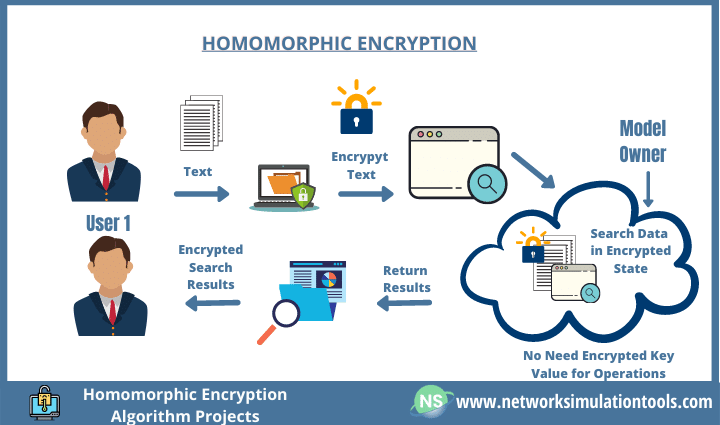
Entropy | Free Full-Text | Towards Secure Big Data Analysis via Fully Homomorphic Encryption Algorithms
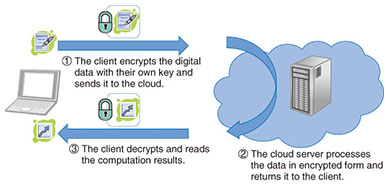
![PDF] HOMOMORPHIC ENCRYPTION IMPLEMENTATION TO ENSURE DATA SECURITY IN CLOUD COMPUTING | Semantic Scholar PDF] HOMOMORPHIC ENCRYPTION IMPLEMENTATION TO ENSURE DATA SECURITY IN CLOUD COMPUTING | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/157535c877fe1f1107ec57745300ff2be9e610b2/6-Figure4-1.png)

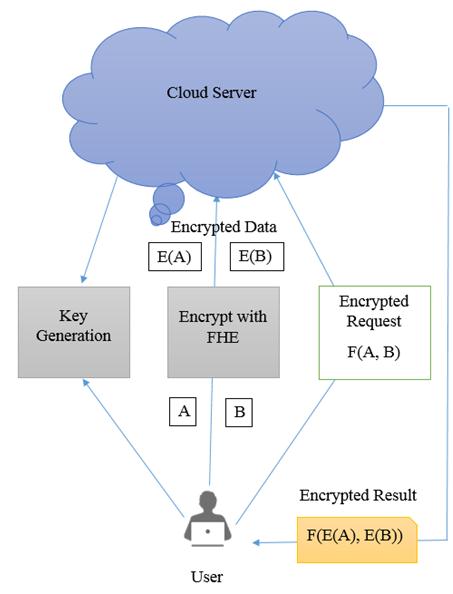
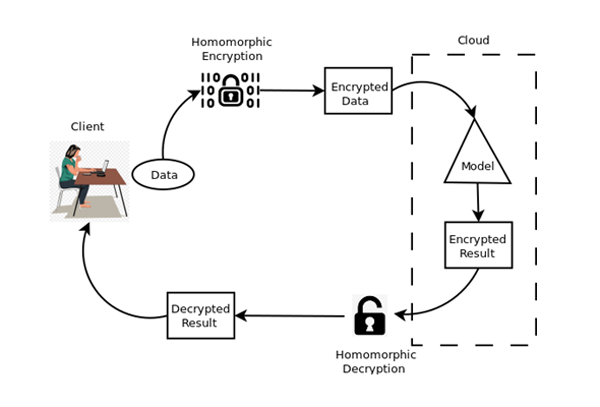


![Homomorphic Encryption Applied to Cloud Computing [17]. | Download Scientific Diagram Homomorphic Encryption Applied to Cloud Computing [17]. | Download Scientific Diagram](https://www.researchgate.net/publication/335697712/figure/fig4/AS:801228523044864@1568039174450/Homomorphic-Encryption-Applied-to-Cloud-Computing-17.jpg)