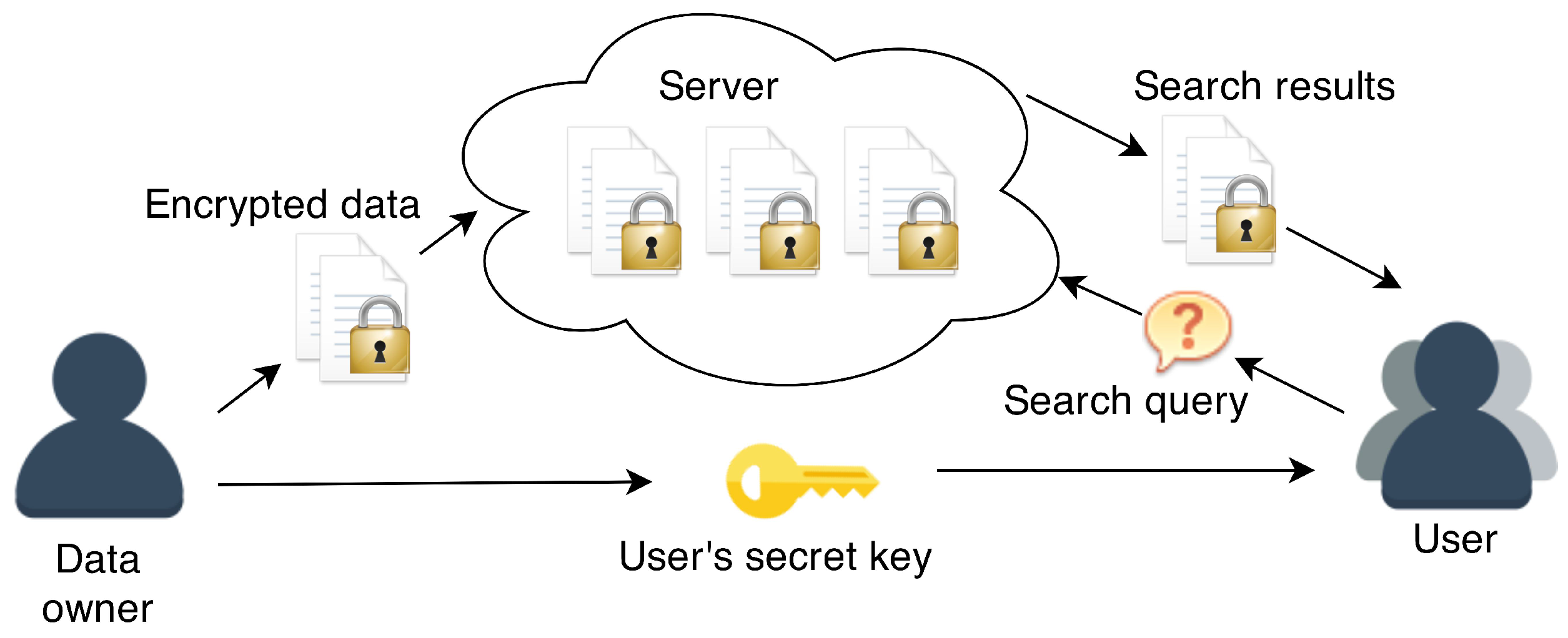
Cryptography | Free Full-Text | Practical Architectures for Deployment of Searchable Encryption in a Cloud Environment

stackconf 2022 | Scaling the Grail – Cloud-Native Computing on Encrypted Data using Carbyne Stack - YouTube
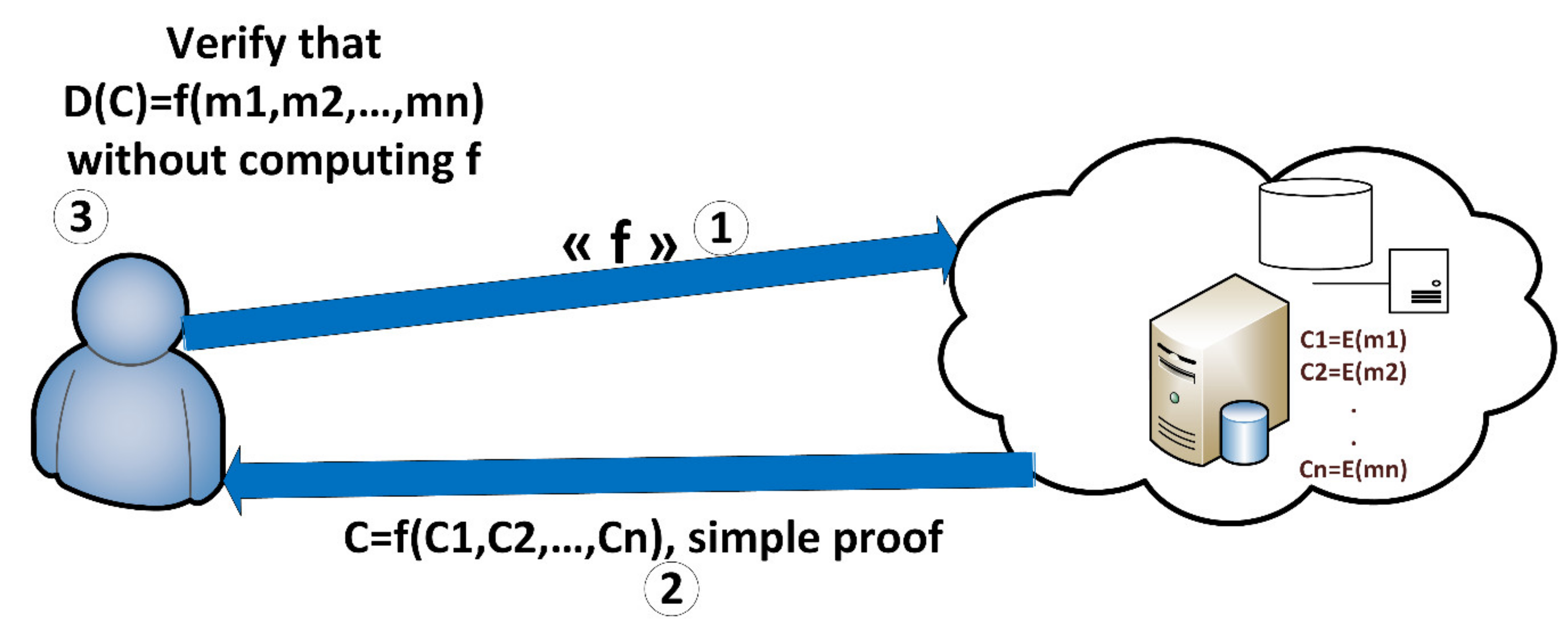
Technologies | Free Full-Text | A Verifiable Fully Homomorphic Encryption Scheme for Cloud Computing Security
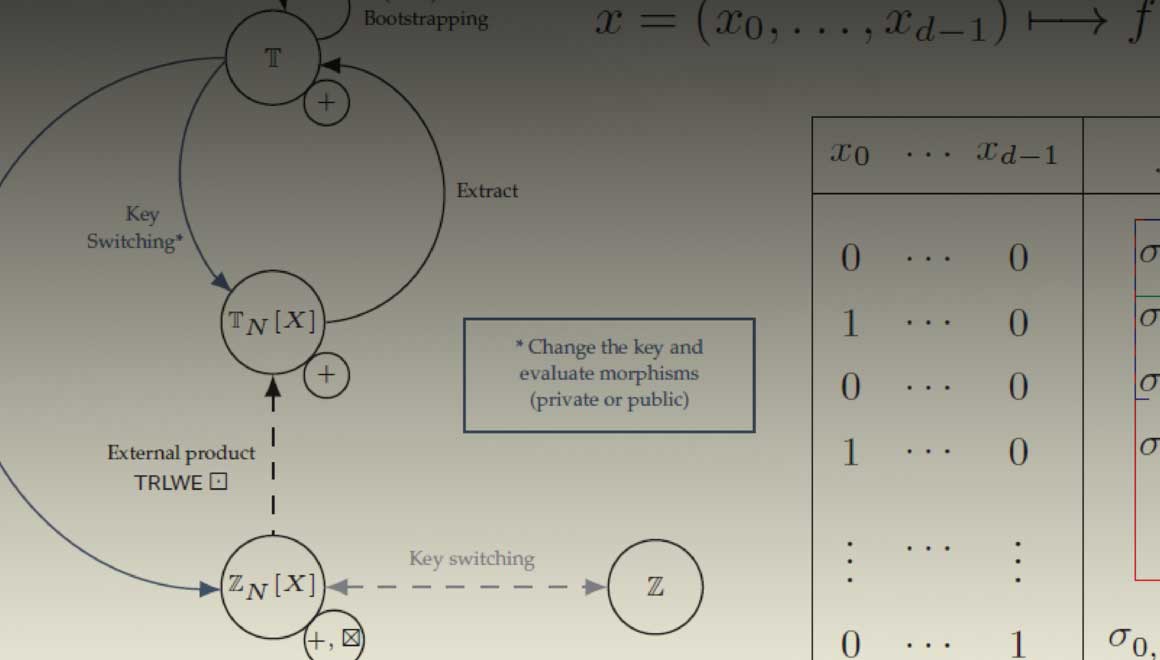
Cornami Partners with Inpher, Pioneer in Secret Computing, to Deliver Quantum-Secure Privacy-Preserving Computing on Encrypted Data
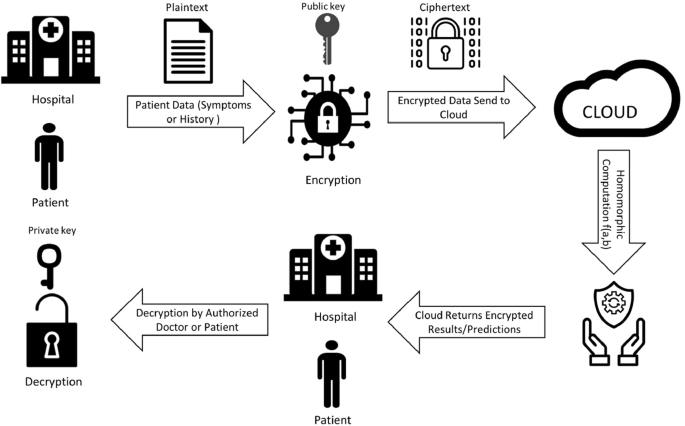
A systematic review of homomorphic encryption and its contributions in healthcare industry | SpringerLink
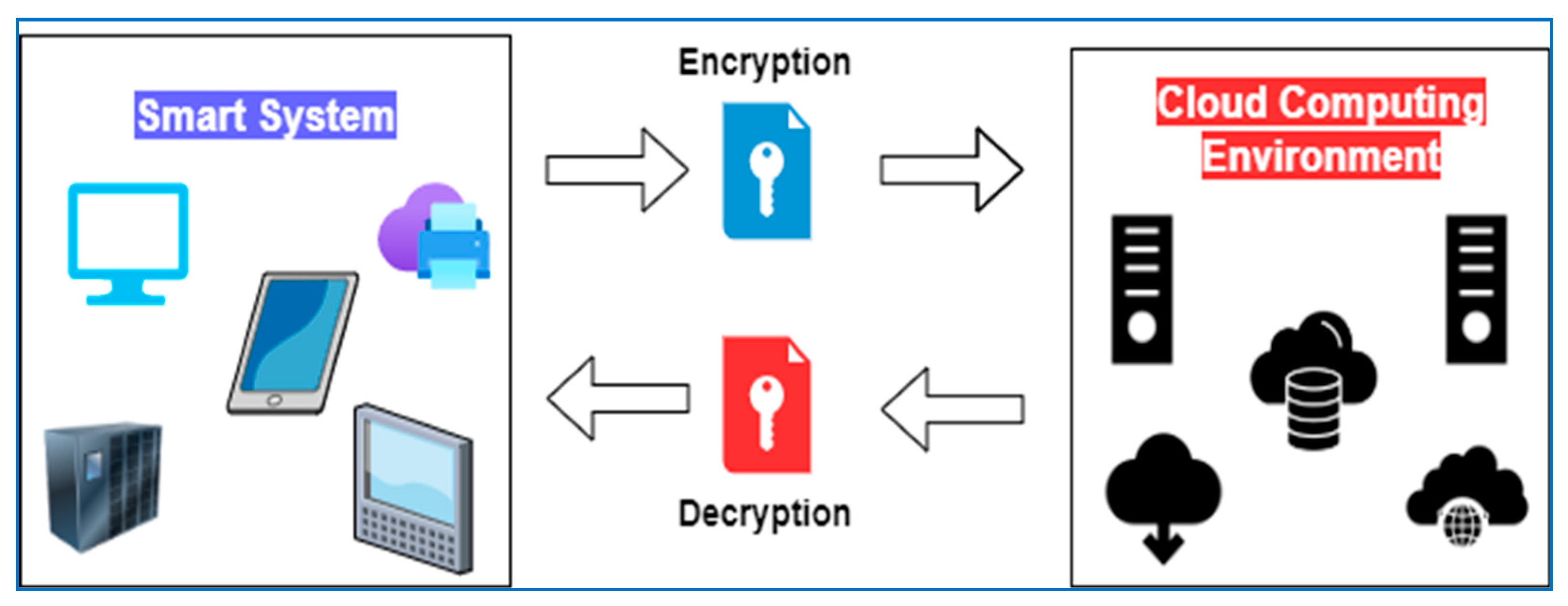
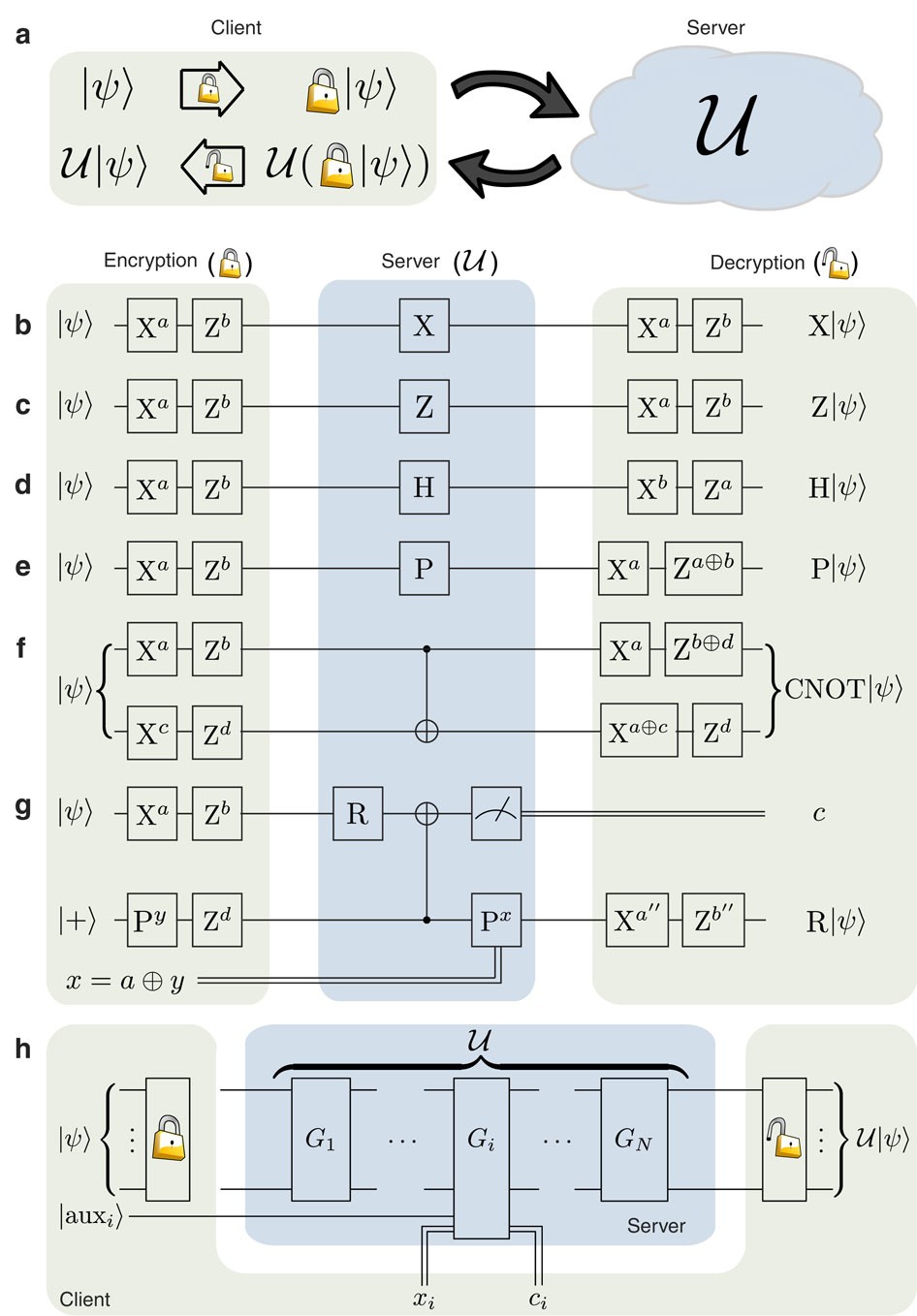



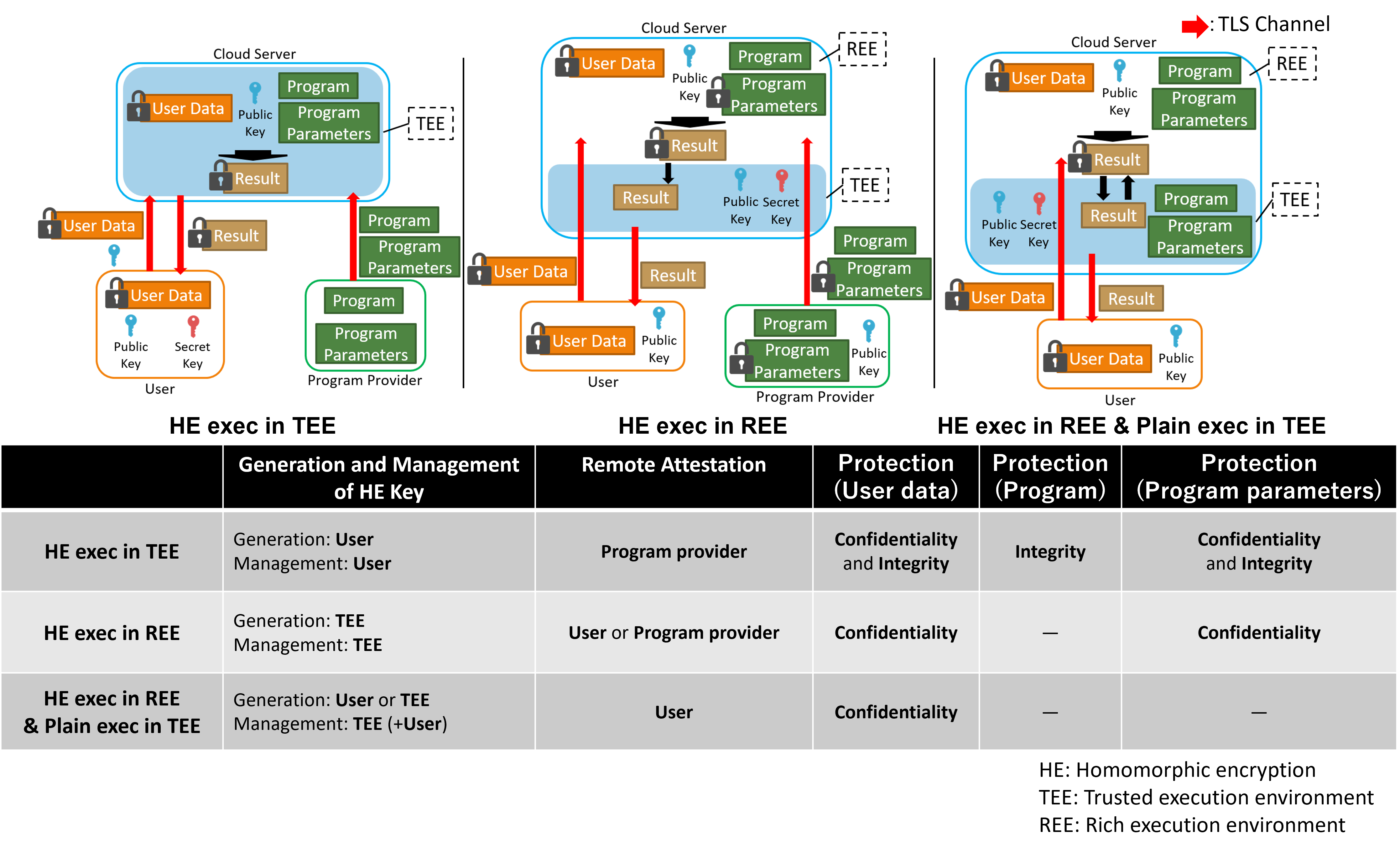

![PDF] Using Fully Homomorphic Encryption to Secure Cloud Computing | Semantic Scholar PDF] Using Fully Homomorphic Encryption to Secure Cloud Computing | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/3d5043584778d6cfbe1aa3f9dd7cb31cc0db6592/5-Figure5-1.png)
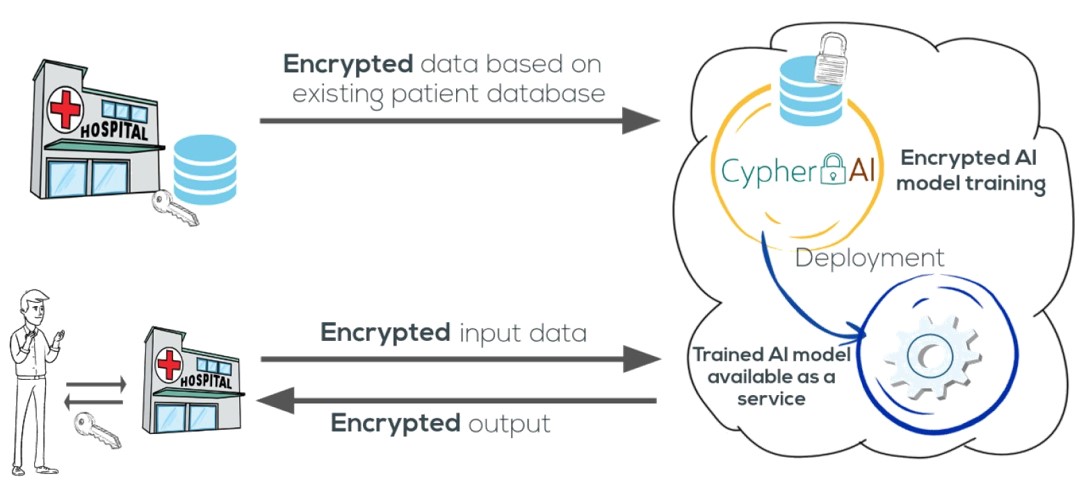
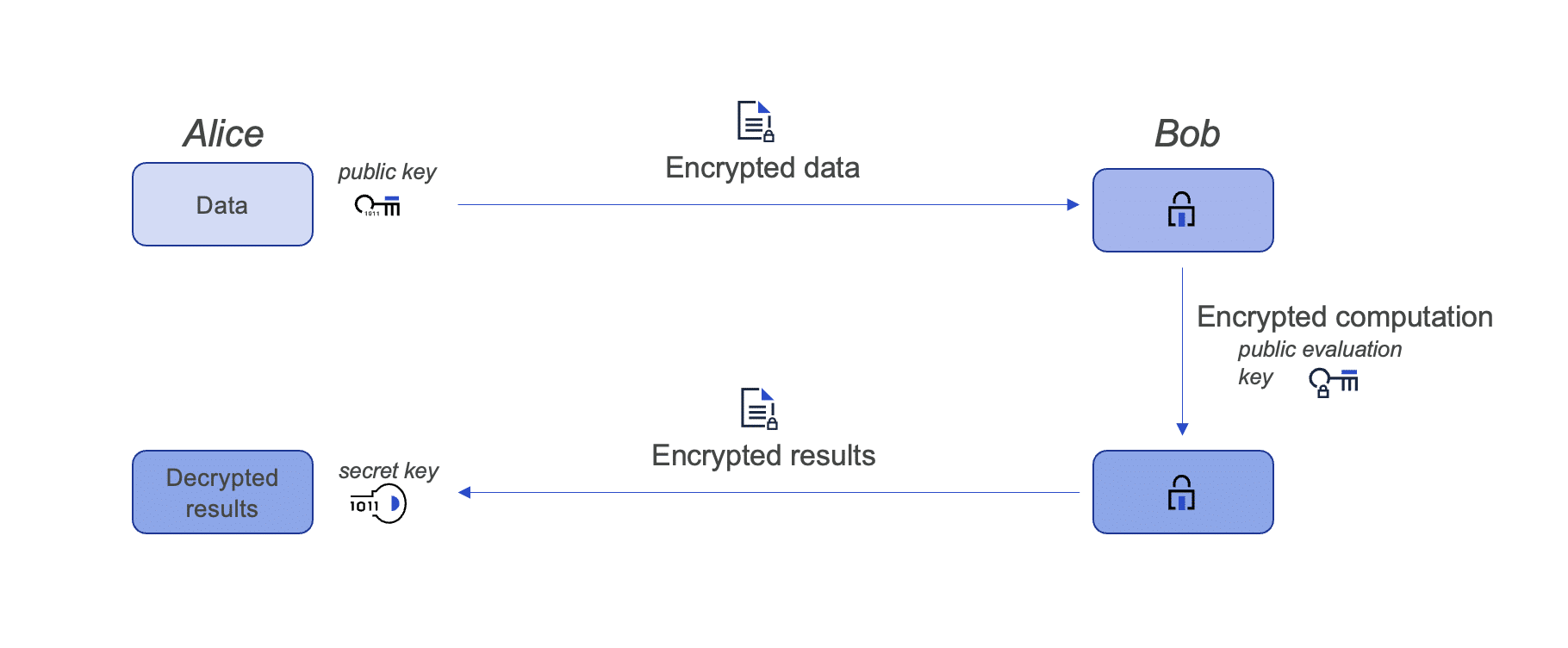




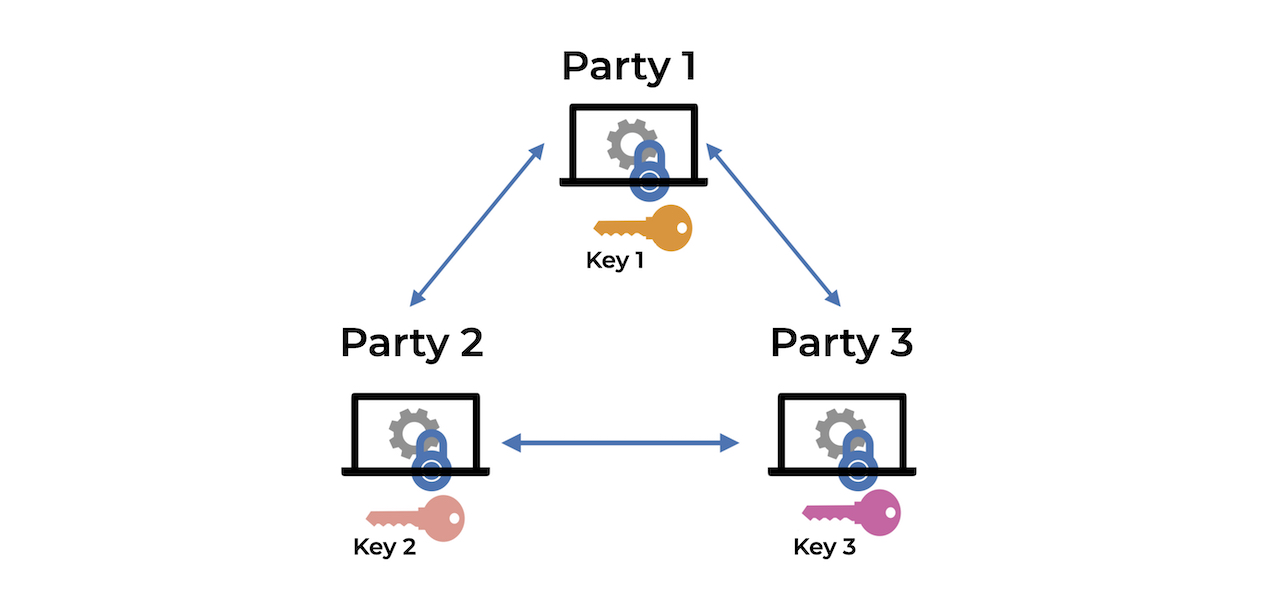


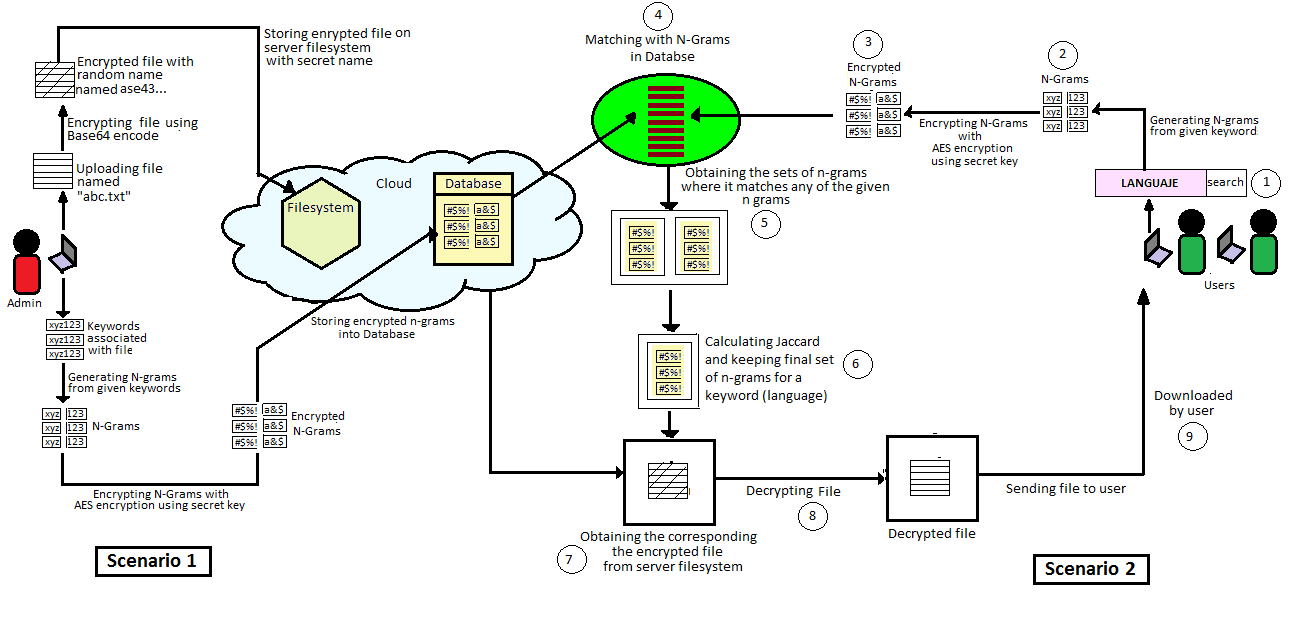

![PDF] Fuzzy Keyword Search Over Encrypted Data in Cloud Computing | Semantic Scholar PDF] Fuzzy Keyword Search Over Encrypted Data in Cloud Computing | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/e14bb18de34c12750da19844c628c332d9c7ce3a/3-Figure1-1.png)