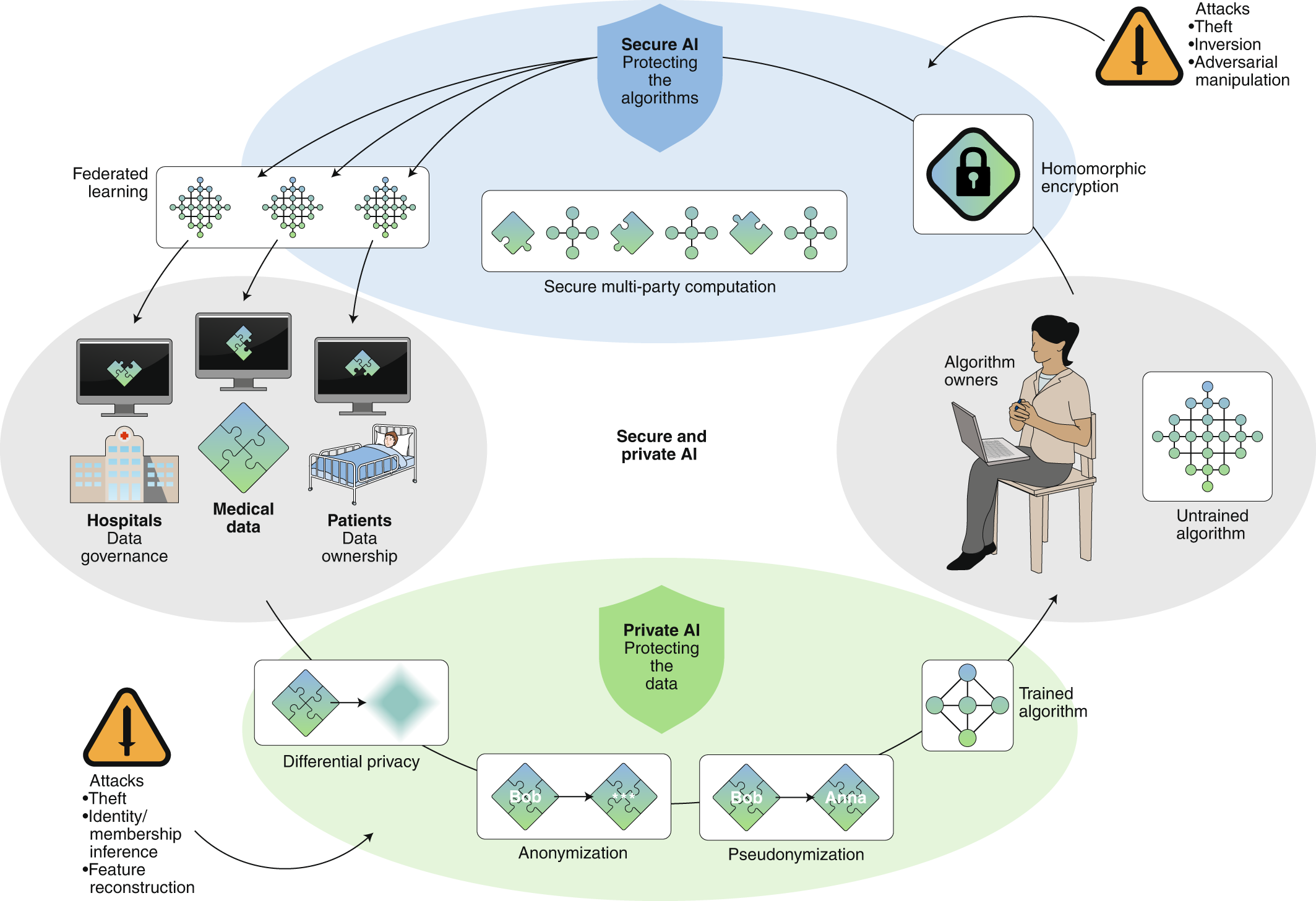
Secure, privacy-preserving and federated machine learning in medical imaging | Nature Machine Intelligence
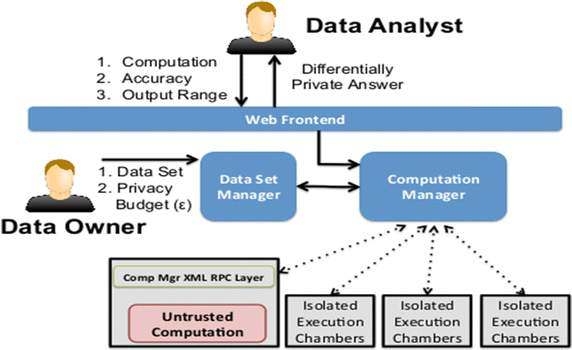
Differential privacy: its technological prescriptive using big data | Journal of Big Data | Full Text
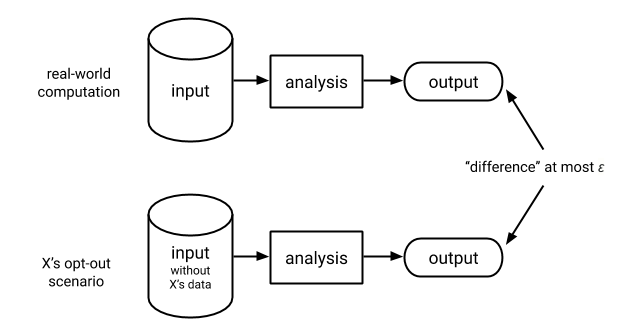
6 Designing Access with Differential Privacy | Handbook on Using Administrative Data for Research and Evidence-based Policy
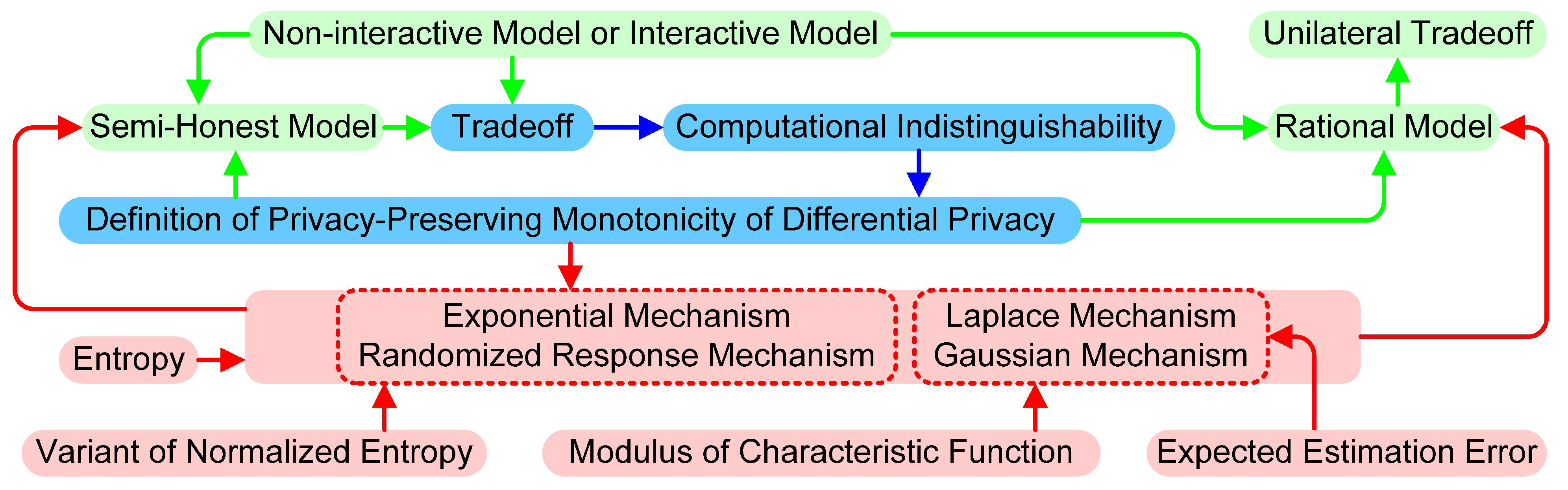
Applied Sciences | Free Full-Text | Privacy-Preserving Monotonicity of Differential Privacy Mechanisms
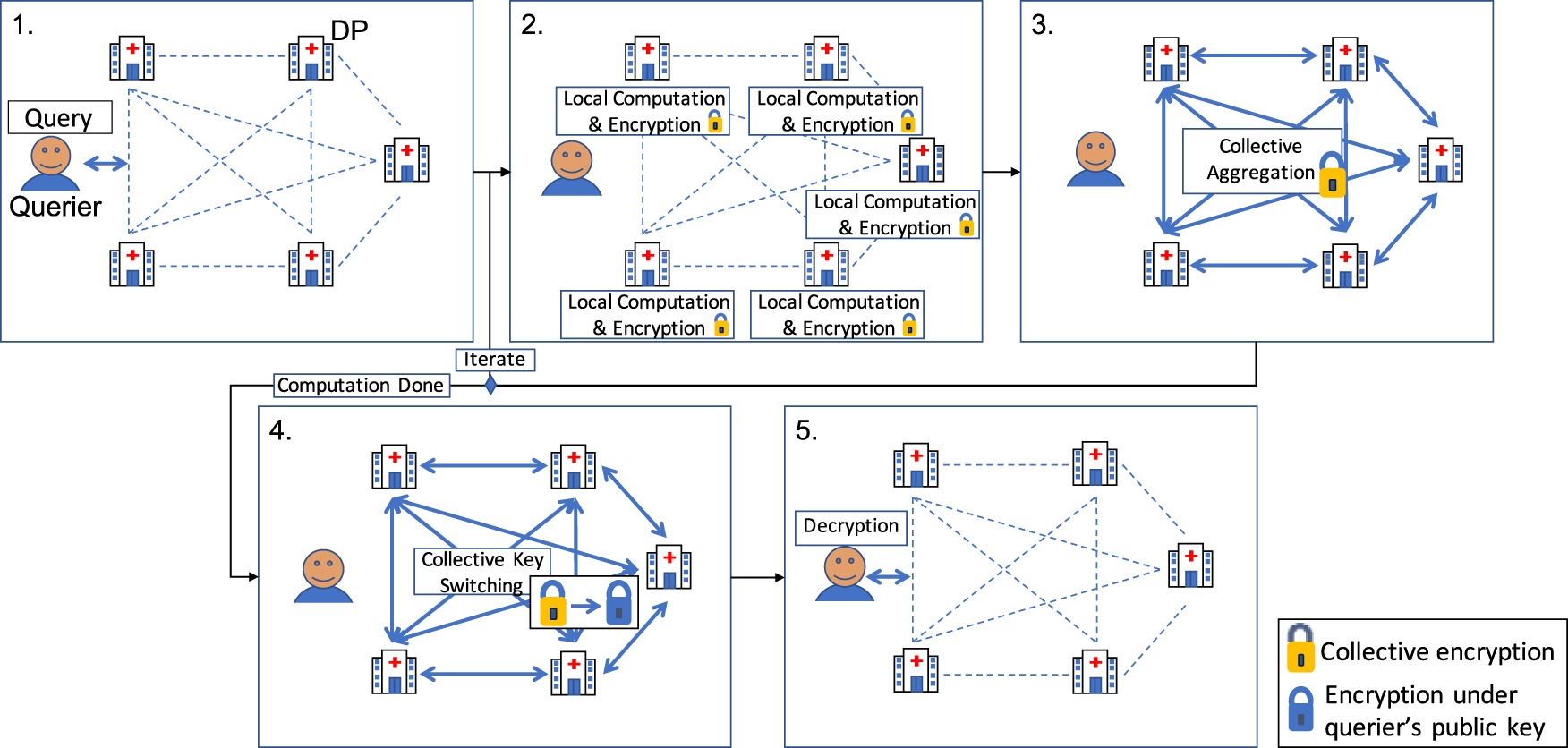
Truly privacy-preserving federated analytics for precision medicine with multiparty homomorphic encryption | Nature Communications

DP-Cryptography: Marrying Differential Privacy and Cryptography in Emerging Applications | February 2021 | Communications of the ACM

Privacy Linter and Opacus: Privacy Attacks and Differentially Private Training Open-Source Libraries - YouTube
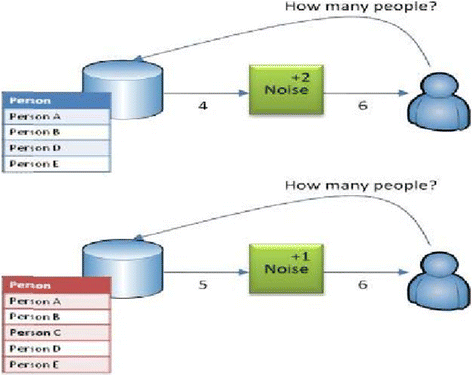
Differential privacy: its technological prescriptive using big data | Journal of Big Data | Full Text

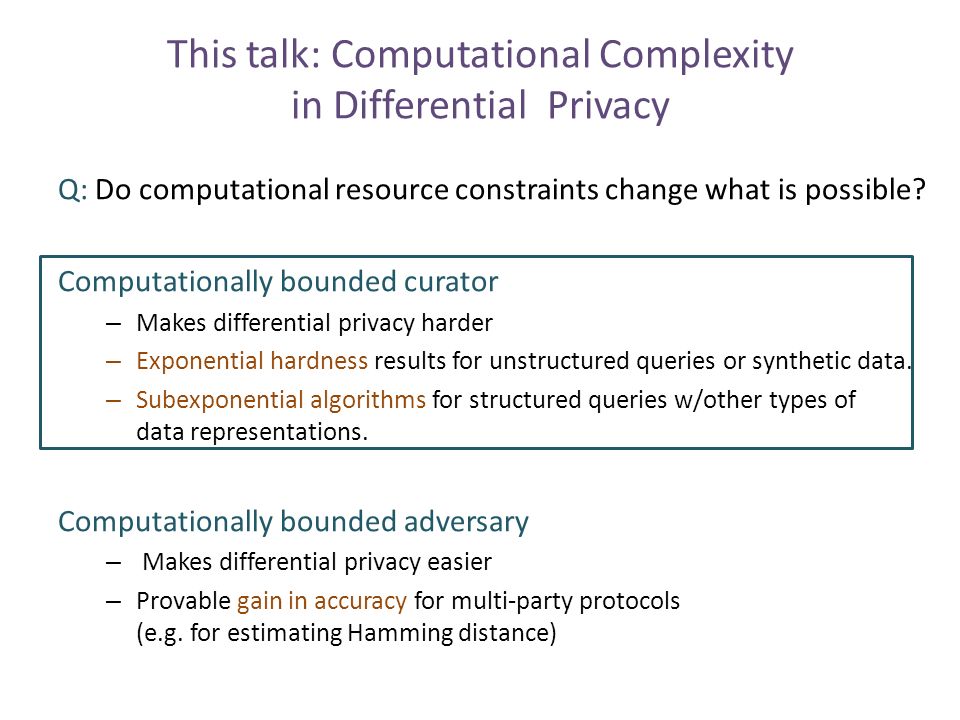
The Complexity of Differential Privacy Salil Vadhan Harvard University TexPoint fonts used in EMF. Read the TexPoint manual before you delete this box.: - ppt download



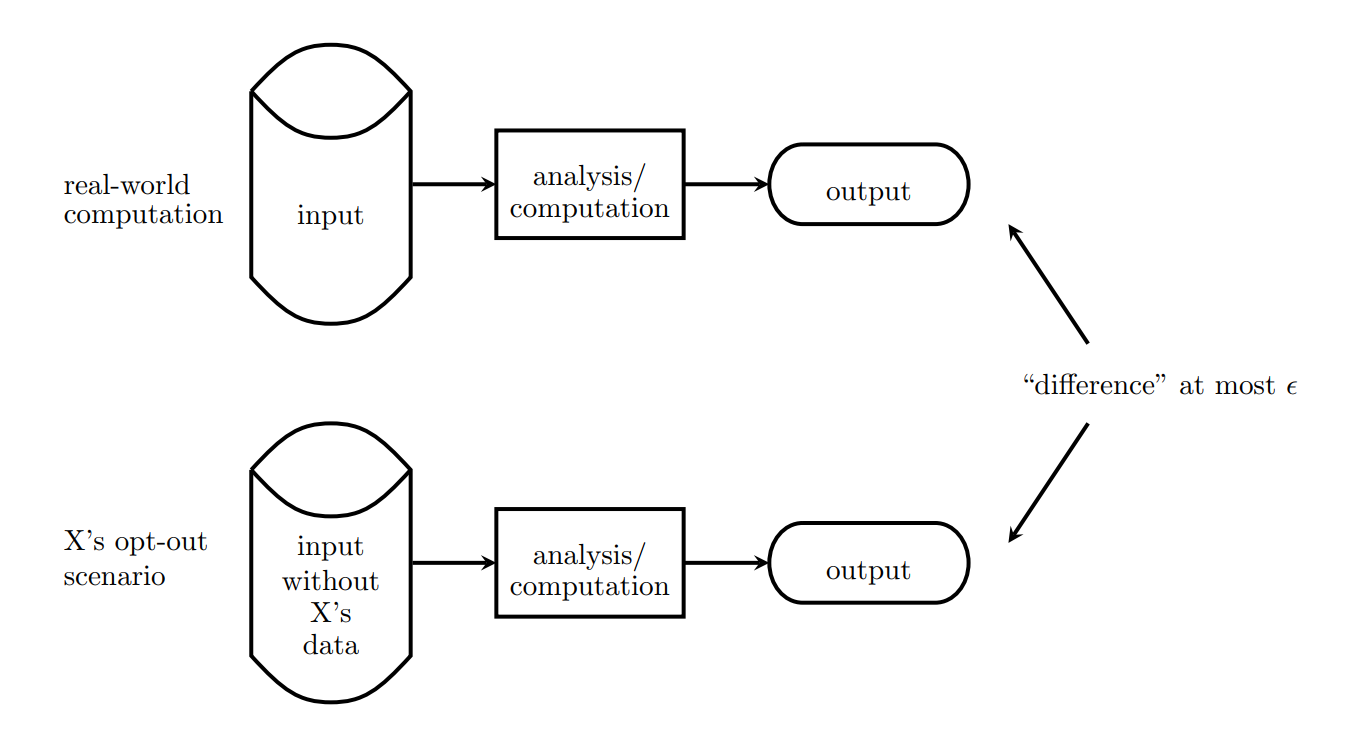

![PDF] SoK: Differential privacies | Semantic Scholar PDF] SoK: Differential privacies | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/74ee8202cb157089efc2697ed64419857e5029e6/3-TableII-1.png)